What is cyber attack how to protect yourself from it
Friends in today’s article I will tell you what is cyber attack how to protect yourself from it, how it can harm you know the full news. So, we are going to talk about cyber attack. Today, at this time when we all have access to internet, we all are connected to the digital world, then many times you would definitely hear this word whose name is cyber attack. Today’s video is going to be a basic video on this cyber attack topic.
What is the concept of cyber attack after all what is the real meaning of cyber attack
In which we will understand that after all this cyber attack topic what is the concept of cyber attack after all what is the real meaning of cyber attack, why are these cyber attacks don what are the disadvantages of cyber attack.But people are threatened by this so let’s start friends and find out what happens eventually This concept of cyber attack is it really so friends we should know this first of all Let us understand that this cyber attack is two words joined together
Cyber means digital world Where we talk about internet and attack means attack then you Understand it
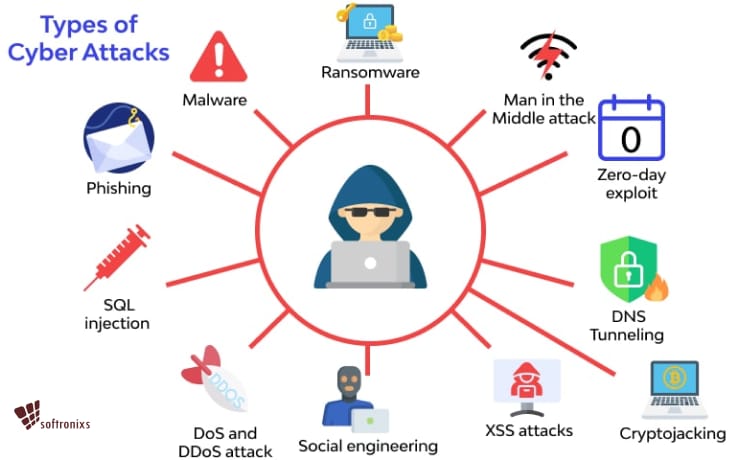
Yes what does this mean friends cyber means digital world Where we talk about internet and attack means attack then you Understand it in such a way that whenever an attack is carried out on your computer or any internet system by some third person Yes without your consent we call it cyber attack You can understand this through a very simple example that there is a company in which 1000 people work All of them have their own computer systems inside those computer systems there is important data of the company and data .
Then some hacker some third person hacks all those computers and steals the data company information
Then some hacker some third person hacks all those computers and steals the data company information present inside those computers cheats with it and deletes it So the situation which occurs we call it cyber attack When a computer is attacked by some other person in an unauthorized manner What should be done its access should be taken friends in this cyber attack what methods are used in which especially when we talk we come across fishing attacks malware attacks password attacks .
These are the internal threads what methods Through which this situation called cyber attack is created
These are the internal threads what methods Through which this situation called cyber attack is created friends now let us understand this cyber attack Why should it be done Let us know what is the motive behind it there are two types of motives behind it in which the first one is for financial gain i.e. any way of earning money friends today At that time there are many such companies which have very important details about the people Like their bank details are considered very important
Now any hacker can steal the structure of some company tomorrow and sell it to some other company and exchange it
Now any hacker can steal the structure of some company tomorrow and sell it to some other company and exchange it for that and earn money Sometimes these cyber attacks are done for games and sometimes these are political morale through it Like if the image of any person some organization or any government has to be spoiled then a propaganda is spread on social media also through our tools Yes the UN runs a propaganda against everyone and this propaganda can be run together on thousands of lakhs of computers and thousands of accounts if the cyber attack has reached them then in this way this cyber attack is done through these two methods in which financial and political motives are involved Friends I hope now it will be clear to you that eventually this concept of cyber attack what it is and such information.
